Guaranteed memory and SWAP are two of the most important parameters that affect the performance of a Linux system.
Guaranteed memory is the amount of memory that will be allocated to a virtual machine and is independent of the available memory on the host.
The process of guaranteed memory works by adding a hardware layer to the system called a memory controller hub. This hardware provides a buffer for the system where it can store data and retrieve it when needed. This buffer is non-power dependent, which means that it will not lose data in the event of a power outage or power failure.
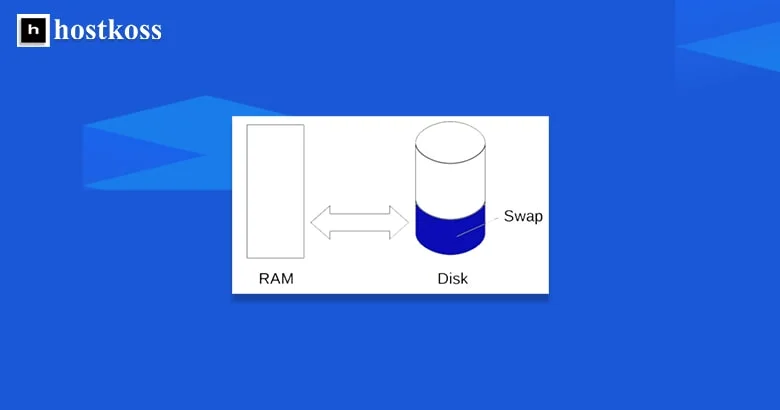
SWAP is another type of virtual memory that is used when there is not enough RAM to store all the data.
The operating system uses SWAP to store less active applications. These applications are automatically moved to the hard disk when they are not in use. This is done to free up memory space for the currently running application.
Less active applications can be anything that does not require immediate attention, such as a word processor or spreadsheet.
Read also:
- What is a VDS/VPS server, and how to choose the best one
- Choosing the best OS for your server: CentOS vs Ubuntu
- Configuring HTTP/2 support in Nginx on Ubuntu 18.04
Questions and answers about guaranteed memory and SWAP
Guaranteed memory ensures consistent access and performance for specific applications by dedicating a fixed amount of physical memory exclusively to their use.
SWAP, or virtual memory, extends the available memory capacity by utilizing disk space as an extension of physical RAM, providing a flexible mechanism for managing memory overflow.
Yes, guaranteed memory and SWAP can complement each other in memory management strategies, with guaranteed memory providing stability and predictability for critical applications, while SWAP offers flexibility and scalability to handle memory overflow.
Workload characteristics, system requirements, and scalability considerations are key factors influencing the selection between guaranteed memory and SWAP, with each option offering unique advantages based on specific use cases and requirements.
Memory leaks can be detected through thorough monitoring and memory profiling techniques, and resolved by identifying and addressing problematic code or memory allocation patterns within applications.
Common optimization strategies include monitoring and analysis of memory usage, utilization optimization techniques such as memory overcommitment and transparent page sharing, and tuning system parameters to optimize memory performance and efficiency.